Cisco AnyConnect 4.7.x and prior. Cisco and Pulse Secure have not publicly acknowledged the issues. Enterprise VPN apps from Check Point and pfSense were deemed safe. Jan 12, 2017 The Cisco $35K solution was going to perform at 400M/s (max, slower with any form of IPS) and our pfSense is yielding 800M/s with AV and some light IPS enabled - CPU runs nicely at 8-10% (then again it's a VM running on a XEON Quad-core with 16GB of RAM.) And, the pfSense config for the ACLs/Routing is so much easier to manage than the PIX/ASA. Researched Cisco ASA Firewall but chose pfSense: Feature-rich, well documented, and there is good support available online pfSense prevents unwanted access. If you configured things properly then you'll be protected to some level. There is still a need for products like. OpenConnect is a SSL VPN client initially created to support Cisco’s AnyConnect SSL VPN. It has since been ported to support the Juniper SSL VPN which is now known as Pulse Connect Secure. Palo Altos Global Protect will also be supported in future and of course the own OpenConnect Server.
With organizations embracing dynamic work culture stakeholders now access the company intranet from the comforts of their home or from public networks or subsidiary sites through VPNs. Network administrators now need to monitor the activities being performed over the VPN and report on VPN. From the compliance and auditing perspective, you would like to see who connects, when, and what are the activities being performed. There is also a necessity for regular VPN audit reports.
Firewall Analyzer will be very handy for the above such requirements since you will be able to obtain Security Reports like 'Denied Attempts', 'Compromising Attempts', 'Attacks', and 'Port Scans', as well as auditing reports like 'Top VPN Users', 'Top failed vpn logins' etc.
The VPN reporting capability of Firewall Analyzer supports both Remote Host VPNs (PPTP,L2TP, and IPSEC) and Site-to-Site VPNs from vendors like Cisco, SonicWALL, WatchGuard, NetScreen, and others.
VPN Reports
Cisco Anyconnect Log In
VPN Reports give detailed statistics on VPN usage, thus Firewall Analyzer acts as a VPN Monitor. VPN usage reports include drill down details on top VPN hosts, top protocols used by the VPN, and bandwidth used by the VPN during peak and off-peak hours. Trend reports show you VPN usage trends over time.'
Top VPN users reports will be very handy if you have Remote Host VPNs configured in your environment. It basically gives you the users connected to your VPN and the amount of traffic consumed by them.
Top Failed VPN users will be very useful when somebody is trying to compromise your VPN network. Repeated or abnormal failed connections would require a closer look as it might result in attacks.
Top Protocol Groups, gives you an overview of what kind of protocol is used in your VPN network. This will be very useful in the case of Site To Site VPN. Some firewalls produce application layer protocol information in the VPN logs and some might not. For the firewalls that are producing protocol information in the logs, this report can give excellent insights.
When you have multiple VPNs in your network, you will be interested in seeing the amount of traffic that is going to search VPN. VPN usage reports (Site to Site VPN Monitoring) exactly addresses this requirement.
Request for a free personalized demo
User-group VPN Reports
Provides VPN usage details for a group of users with details on number of hits, duration of usage, and total bytes of VPN traffic.
Featured links
Firewall Rule Management
Manage your firewall rules for optimum performance. Anomaly free, properly ordered rules make your firewall secured. Audit the firewall security and manage the rule/config changes to strengthen the security.
Firewall Compliance Management
Integrated compliance management system automates your firewall compliance audits. Ready made reports available for the major regulatory mandates such as PCI-DSS, ISO 27001, NIST, NERC-CIP, and SANS.
Firewall Log Management
Unlock the wealth of network security information hidden in the firewall logs. Analyze the logs to find the security threats faced by the network. Also, get the Internet traffic pattern for capacity planning.
Real-time Bandwidth Monitoring
With live bandwidth monitoring, you can identify the abnormal sudden shhot up of bandwidth use. Take remedial measures to contain the sudden surge in bandwidth consumption.
Firewall Alerts
Take instant remedial actions, when you get notified in real-time for network security incidents. Check and restrict Internet usage if banwidth exceeds specified threshold.
Manage Firewall Service
MSSPs can host multiple tenants, with exclusive segmented and secured access to their respective data. Scalable to address their needs. Manages firewalls deployed around the globe.
With these VPN reports (VPN tracker), security administrators can easily plan an efficient VPN infrastructure that provides the ideal platform for remote employees to work without any hassle. A well-planned VPN infrastructure enables your company to retain its productivity and gain a competitive edge in today's challenging marketplace. Download a free trial of Firewall Analyzer,and get the best out of your VPN infrastructure.
Featured links
This page describes how to configure IPsec to connect pfSense® routerand a Cisco IOS router with IPsec capabilities.
Example Network¶
This diagram shows the specifics of the network where this VPN is beingconfigured. For the sake of this documentation, both hosts were onprivate subnets, but functionally equivalent to two hosts across theInternet.
Configuring the router¶
First, configure the phase 1 settings with a crypto isakmp policy. Thefollowing sets it for 3DES, SHA and group 2 to match the pfSenseconfiguration shown later.
Next, configure the pre-shared key. The key in this example is ABCDEFG,but be sure to use something random and secure for any productiondeployments. 10.0.66.22 is the WAN IP of the pfSense system beingused.
Next configure the transform set for phase 2. This uses ESP, 3DESand SHA. The transform set is named 3DES-SHA, which is how it willbe referred to later.
Now configure an access list that will match the local and remotesubnets on the pfSense router. This is configured as access-list 100,which will be used in the next step. Remember this uses wildcard masks,so a /24 network (255.255.255.0 mask) is represented as 0.0.0.255.
Now configure the crypto map for this VPN:
Lastly, under the interface configuration for the interface where theVPN will terminate (the one with the public IP), assign the crypto map:
The configuration is then finished on the Cisco side.
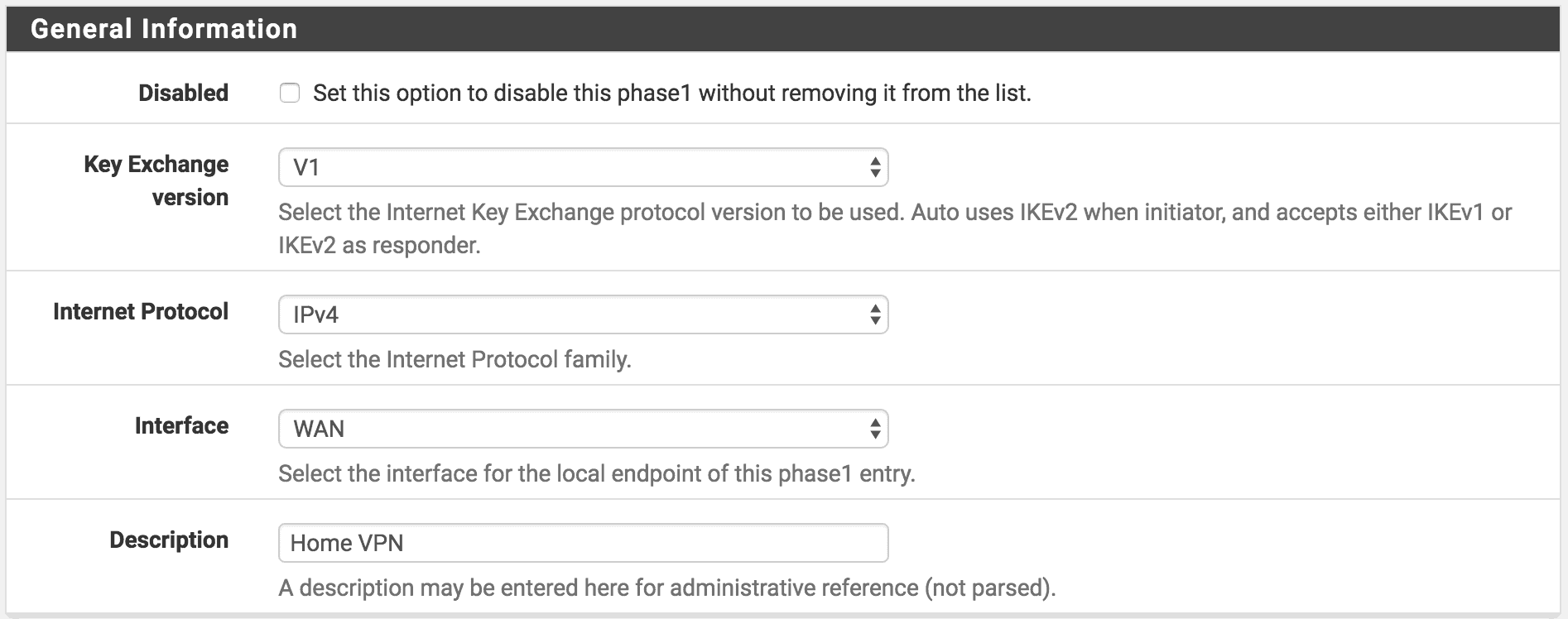
Configuring pfSense Software¶
This screenshot shows the pfSense configuration matching the above Ciscoconfiguration.
In the above example, the pfSense IPsec tunnel should be set as follows:
Phase 1:
Remote Gateway: 10.0.64.175Authentication Method: Pre-Shared KeyNegotiation Mode: MainMy Identifier: My IP AddressPre-Shared Key: ABCDEFGEncryption Algorithm: 3DESHash Algorithm: SHA1DH Key Group: 2Lifetime: 28800NAT Traversal: Disable
It may also be advisable to set Proposal Checking to Obey to avoidsome issues with building a tunnel when the other side initiates.
Phase 2:
Mode: Tunnel IPv4Local Network: LAN SubnetRemote Network: 172.26.5.0/24Protocol: ESPEncryption Algorithm: 3DES (others may also be checked, but besure to leave 3DES checked)Hash Algorithm: SHA1PFS Key Group: 2Lifetime: 3600
Testing the connection¶
Cisco Anyconnect Download Windows 10
To test the connection, from the pfSense router, do the following:
Navigate to Diagnostics > Ping
Enter an IP address on the remote network
Choose the LAN interface
Click Ping.
The initial negotiation may make all three of the first pings timeout,so try it a second time as well. If configured as depicted above, oncethe tunnel connects, the following will be seen:
Troubleshooting¶
If the connection doesn’t come up, there is a mismatch somewhere in theconfiguration. Depending on specifics, more useful information may beobtained from pfSense router or the Cisco router. Checking logs on bothends is recommended. For pfSense software, browse toStatus > System Logs on the IPsec tab. For Cisco, rundebug crypto isakmp and term mon (if not connected via serialconsole) to make the debug messages appear in a session. The outputcan be verbose, but will usually tell specifically what was mismatched.
“No NAT” List on Cisco IOS¶
Pfsense Cisco Anyconnect Login
It may also be necessary to tell Cisco IOS not to NAT the traffic thatis destined for the IPsec tunnel. There are several ways to accomplishthis, depending on how the router has NAT configured. If the followingexample does not help, there are several examples that turn up in aGoogle search for “cisco ios nonat ipsec”:
Pfsense Cisco Anyconnect Client
This will direct the router to prevent NAT if the traffic is going fromthe subnet behind the Cisco router to the subnet behind the pfSenserouter, but allow it in all other cases.
